12 Unc Email Security Protocols To Protect Your Data

In today's digital landscape, ensuring the security of your sensitive data is of utmost importance. As cyber threats continue to evolve, it is crucial to implement robust email security protocols to safeguard your organization's information. This comprehensive guide will delve into 12 essential email security protocols that can help protect your data and mitigate the risks associated with email communication.
Understanding the Importance of Email Security

Email is a fundamental communication channel for businesses and individuals alike. However, it also presents a significant security challenge due to its widespread use and potential vulnerabilities. Cybercriminals often target email systems to gain access to sensitive information, launch phishing attacks, or spread malware. Implementing robust email security measures is essential to prevent data breaches, protect your reputation, and maintain the trust of your clients and customers.
The 12 Essential Email Security Protocols
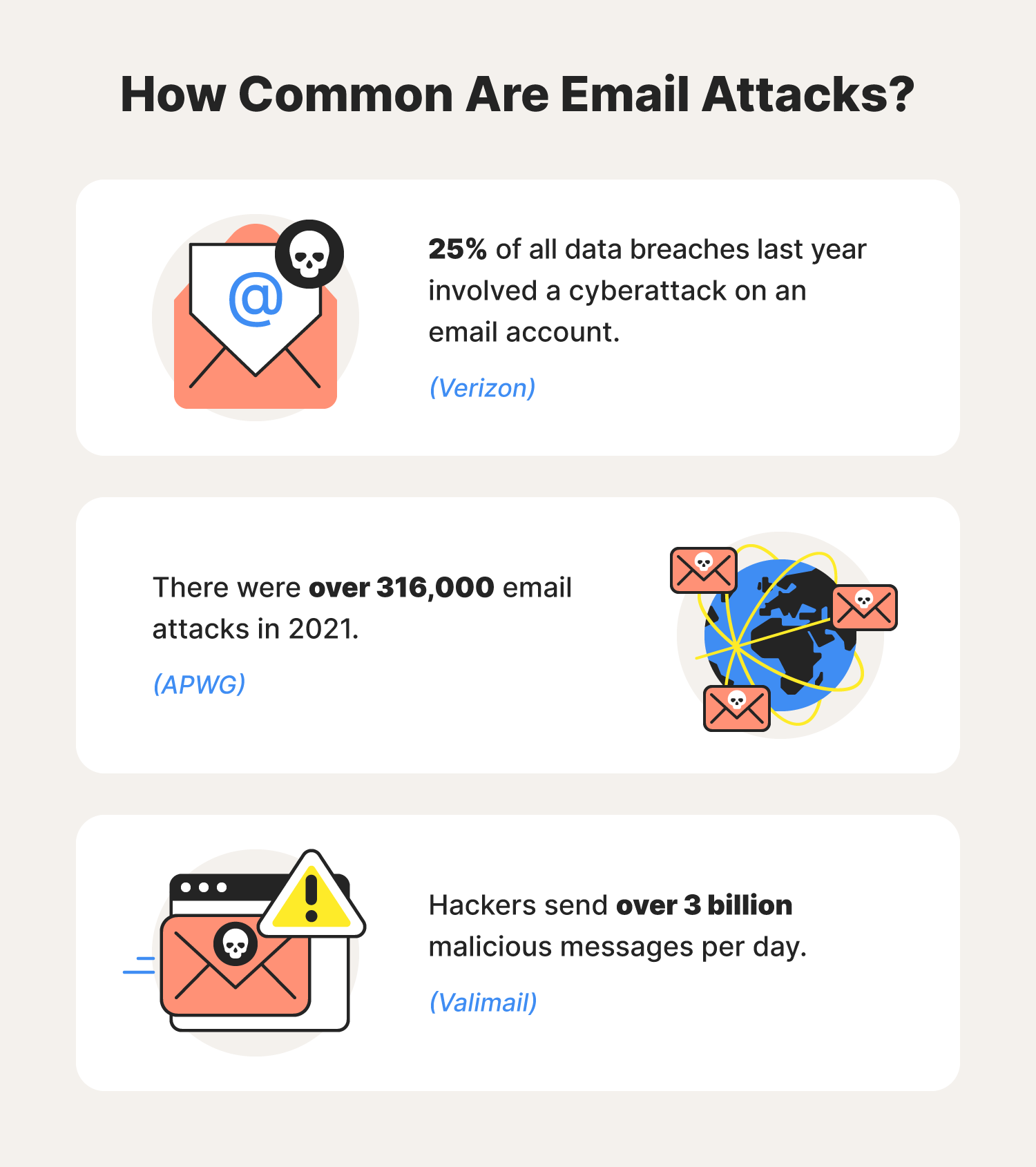
To fortify your email security posture, consider implementing the following protocols:
1. Email Encryption
Email encryption ensures that the content of your emails remains secure and unreadable to unauthorized individuals. By using encryption protocols like Secure/Multipurpose Internet Mail Extensions (S/MIME) or Pretty Good Privacy (PGP), you can protect the confidentiality of your messages during transmission.
2. Secure Email Gateways
Secure email gateways act as a barrier between your internal network and the external email environment. These gateways scan incoming and outgoing emails for potential threats, such as malware, phishing attempts, or spam. By implementing a robust email gateway solution, you can filter out malicious content and prevent it from reaching your organization.
3. Spam Filtering
Spam filtering is a crucial component of email security. Advanced spam filters can identify and block unwanted or malicious emails before they reach your inbox. By analyzing email content, headers, and sender reputation, these filters help reduce the risk of phishing attacks and malware infections.
4. Anti-Phishing Measures
Phishing attacks are a common threat in the email landscape. Implement anti-phishing measures, such as email authentication protocols like Domain-based Message Authentication, Reporting, and Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM). These protocols help verify the authenticity of incoming emails and reduce the likelihood of successful phishing attempts.
5. Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to your email accounts. By requiring users to provide a second form of authentication, such as a unique code sent to their mobile device, you can prevent unauthorized access even if their password is compromised.
6. User Education and Awareness
One of the most effective email security measures is user education. Train your employees to recognize potential threats, such as suspicious email attachments, links, or requests for sensitive information. Regular security awareness training can significantly reduce the risk of successful cyber attacks within your organization.
7. Email Content Scanning
Implement email content scanning to detect and block malicious attachments or links. Advanced scanning tools can analyze the content of emails, including attachments, to identify and quarantine potential threats before they can cause harm.
8. Secure Email Archiving
Secure email archiving ensures that your organization’s email data is safely stored and protected. By implementing a robust email archiving solution, you can retain important emails, comply with regulatory requirements, and facilitate easy access to historical email data while maintaining security.
9. Email Policy Enforcement
Establish and enforce clear email usage policies within your organization. Define guidelines for acceptable email practices, such as prohibiting the sharing of sensitive information via email or limiting the use of personal email accounts for work-related purposes. Regularly communicate and enforce these policies to ensure compliance.
10. Email Backup and Disaster Recovery
Implementing a robust email backup and disaster recovery strategy is essential to protect your organization’s email data. Regularly back up your email servers and ensure that the backups are stored securely off-site. In the event of a data loss or system failure, a well-planned backup and recovery process can help minimize downtime and ensure business continuity.
11. Email Monitoring and Analysis
Continuous monitoring and analysis of your email infrastructure can help identify potential security breaches or anomalies. Use security information and event management (SIEM) tools to detect suspicious activities, such as unusual email traffic patterns or unauthorized access attempts. By analyzing these insights, you can take proactive measures to strengthen your email security posture.
12. Regular Security Audits and Updates
Conduct regular security audits to assess the effectiveness of your email security measures. Stay updated with the latest security patches and updates for your email servers, software, and security solutions. Regularly review and update your security policies to address emerging threats and vulnerabilities.
Real-World Application and Benefits
Implementing these email security protocols offers a range of benefits, including:
- Enhanced Data Protection: By encrypting emails and implementing secure gateways, you can safeguard sensitive information from unauthorized access.
- Reduced Cyber Risks: Robust email security measures help mitigate the risks of phishing, malware, and other cyber threats, protecting your organization's reputation and assets.
- Compliance with Regulations: Many industries have strict data protection regulations. Implementing email security protocols ensures compliance with these regulations and helps avoid legal consequences.
- Improved Business Continuity: With secure email archiving and backup solutions, your organization can quickly recover from data loss or system failures, minimizing downtime and ensuring uninterrupted operations.
Conclusion
Email security is a critical aspect of overall cybersecurity. By implementing the 12 essential email security protocols outlined in this guide, you can significantly strengthen your organization’s defenses against email-based threats. Remember that email security is an ongoing process, and regular updates, monitoring, and user education are vital to staying ahead of evolving cyber threats.
What is the role of user education in email security?
+User education plays a crucial role in email security. By training employees to recognize potential threats, such as phishing attempts or suspicious attachments, you can significantly reduce the risk of successful cyber attacks. Regular security awareness training empowers your team to make informed decisions and take proactive measures to protect your organization’s data.
How often should I update my email security protocols?
+It is essential to keep your email security protocols up to date to address emerging threats and vulnerabilities. Regularly review and update your security measures, including software patches, spam filters, and anti-malware solutions. Aim to conduct security audits and updates at least annually or more frequently if new threats are identified.
What are some best practices for email encryption?
+When implementing email encryption, consider the following best practices: use strong encryption algorithms, such as AES-256; ensure that both the sender and recipient have the necessary encryption keys; and consider using digital certificates to verify the identity of the sender. Additionally, educate your users on the importance of secure email practices to maintain the integrity of encrypted communications.



