15+ Stepbystep Guide To Secure Uc Login

In today's digital age, ensuring the security of your online accounts is paramount. With the increasing prevalence of cyber threats, it's crucial to take proactive measures to protect your sensitive information. In this comprehensive guide, we will walk you through the step-by-step process of securing your UC (University of California) login, providing you with the knowledge and tools to fortify your online presence.
Understanding the Importance of UC Login Security
The University of California (UC) system is a renowned academic institution, and your UC login serves as the gateway to a wealth of resources and personal data. From accessing academic records to managing financial information, the security of your UC login is essential to safeguard your privacy and prevent unauthorized access.
In recent years, the UC system has taken significant steps to enhance login security, implementing robust authentication protocols and providing users with additional layers of protection. By following this guide, you can ensure that your UC login remains secure and inaccessible to malicious actors.
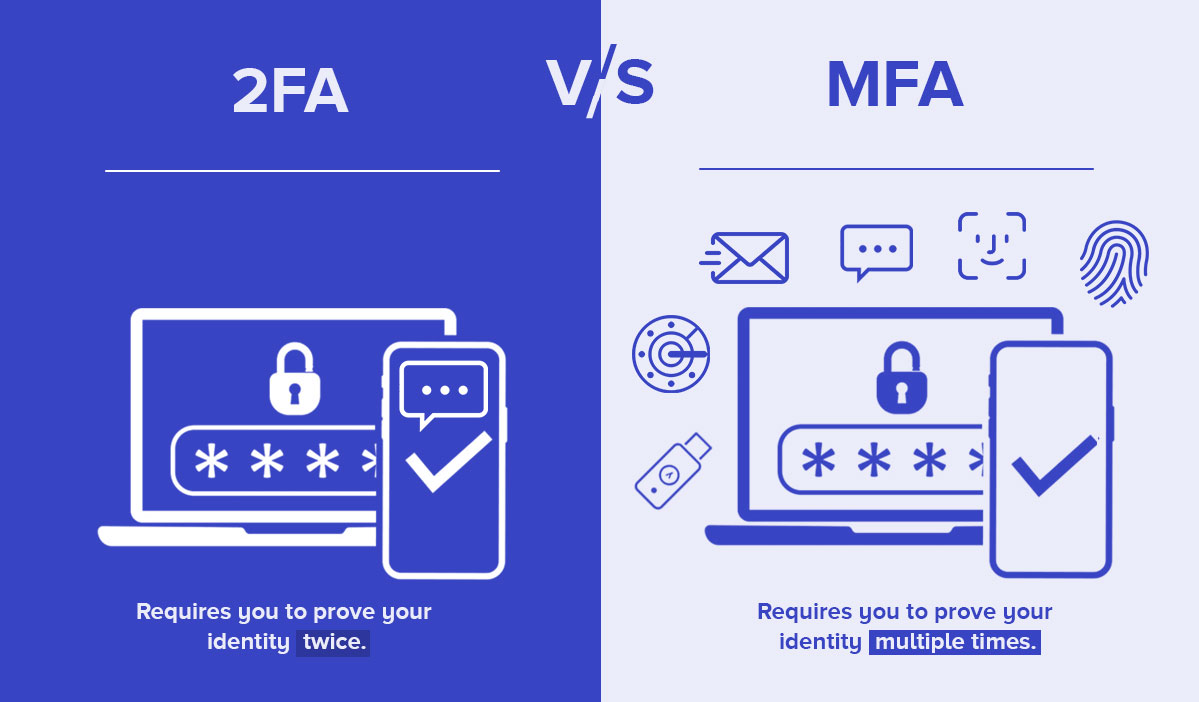
Step 1: Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a critical security measure that adds an extra layer of protection to your UC login. By enabling 2FA, you ensure that even if your password is compromised, unauthorized access to your account is highly unlikely.
- Log in to your UC account using your username and password.
- Navigate to the "Security Settings" or "Account Settings" section of your UC profile.
- Locate the "Two-Factor Authentication" or "2FA" option and click on it.
- Follow the instructions provided by the UC system to set up 2FA. This typically involves choosing an authentication method, such as receiving a text message or using an authentication app.
- Enter the verification code or use the authentication app to complete the setup process.
By enabling 2FA, you significantly reduce the risk of unauthorized access, as an additional verification step is required to log in to your UC account.
Tips for Effective 2FA
- Choose a reliable authentication app, such as Google Authenticator or Authy, to generate time-based one-time passwords (TOTP) for added security.
- Keep your backup codes in a safe place, as they can be used to access your account if you lose access to your primary authentication method.
- Regularly review and update your 2FA settings to ensure they remain secure and up-to-date.
Step 2: Create a Strong and Unique Password
A strong and unique password is the foundation of a secure UC login. Avoid using easily guessable passwords, such as your name, birthdate, or common phrases. Instead, opt for a combination of uppercase and lowercase letters, numbers, and special characters.
- Visit the UC password management page or navigate to the "Password Settings" section of your UC profile.
- Click on the "Change Password" or "Update Password" option.
- Enter your current password and create a new, strong password that meets the UC's password requirements.
- Re-enter the new password to confirm.
- Click on the "Save" or "Update" button to finalize the password change.
Remember to avoid using the same password for multiple accounts. Consider using a password manager to generate and store unique, complex passwords for all your online accounts.
Password Best Practices
- Use a password that is at least 12 characters long and includes a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable information, such as your name, birthdate, or pet’s name, in your password.
- Regularly update your password, especially if you suspect any security breaches or if you have shared your password with others.
Step 3: Enable Login Notifications
Enabling login notifications is an effective way to stay informed about any unauthorized access attempts to your UC account. By receiving real-time alerts, you can quickly take action to secure your account and prevent potential data breaches.
- Log in to your UC account and navigate to the "Security Settings" or "Account Notifications" section.
- Locate the "Login Notifications" or "Account Activity Alerts" option and enable it.
- Choose your preferred notification method, such as email, text message, or push notification.
- Review the settings to ensure you receive notifications for all login attempts, including successful and unsuccessful ones.
By enabling login notifications, you can quickly identify any suspicious activity and take immediate action to protect your UC account.
Step 4: Regularly Review and Update Your Security Settings

Maintaining a secure UC login requires regular attention and updates to your security settings. It’s essential to review and adjust your settings periodically to adapt to changing security landscapes and emerging threats.
- Log in to your UC account and access the "Security Settings" or "Account Settings" section.
- Review the current security measures, such as 2FA, password settings, and login notifications.
- Update any outdated or weak security settings, such as changing your password or enabling additional authentication methods.
- Consider adding extra security measures, such as enabling biometric authentication or setting up a backup email address for password recovery.
By regularly reviewing and updating your security settings, you can ensure that your UC login remains secure and resilient against evolving cyber threats.
Step 5: Use a Secure Device and Network
The security of your UC login also depends on the device and network you use to access your account. Ensure that you are using a secure device with up-to-date antivirus software and regular security updates.
- Use a trusted and secure device, such as a personal computer or a mobile device with robust security measures.
- Connect to a secure network, preferably using a VPN (Virtual Private Network) to encrypt your internet traffic and protect your data.
- Avoid accessing your UC account on public or unsecured Wi-Fi networks, as they may expose your data to potential vulnerabilities.
By using a secure device and network, you can minimize the risk of unauthorized access and data breaches.
Step 6: Enable Password Recovery Options
Password recovery options are crucial in case you forget your UC login password or if your account is compromised. By setting up reliable recovery methods, you can quickly regain access to your account and prevent unauthorized changes.
- Log in to your UC account and navigate to the "Password Recovery" or "Account Recovery" section.
- Choose at least two reliable recovery methods, such as a backup email address, a mobile phone number, or security questions.
- Ensure that the recovery information is up-to-date and easily accessible.
- Consider adding additional recovery methods, such as linking your UC account to a trusted social media account.
By enabling password recovery options, you can ensure a smooth and secure process to regain control of your UC account in case of emergencies.
Step 7: Stay Informed about Phishing Scams
Phishing scams are a common tactic used by cybercriminals to trick users into revealing their login credentials. By staying informed and vigilant, you can protect yourself from falling victim to these scams.
- Familiarize yourself with common phishing techniques, such as fake login pages, suspicious emails, or social engineering tactics.
- Be cautious of any unsolicited emails or messages asking for your UC login credentials. Verify the authenticity of the sender before providing any sensitive information.
- Look for signs of a phishing attempt, such as misspelled words, unusual formatting, or urgent language.
- Regularly review the UC's official security guidelines and stay updated on the latest phishing scams and prevention strategies.
By staying informed and practicing caution, you can avoid falling victim to phishing scams and protect your UC login from unauthorized access.
Step 8: Enable Account Lockout after Multiple Failed Attempts
Enabling account lockout after multiple failed login attempts is an effective measure to prevent brute-force attacks and unauthorized access. By locking out the account temporarily, you can prevent automated login attempts and give yourself time to investigate any suspicious activity.
- Log in to your UC account and navigate to the "Security Settings" or "Account Security" section.
- Locate the "Account Lockout" or "Failed Login Attempts" option and enable it.
- Set the number of allowed failed login attempts before the account is locked out. Typically, 3-5 attempts are recommended.
- Determine the duration of the account lockout, ensuring it is long enough to prevent automated login attempts but not overly disruptive to legitimate users.
By enabling account lockout, you can add an extra layer of security to your UC login and deter potential attackers.
Step 9: Use a Password Manager
A password manager is a valuable tool to help you create and manage strong, unique passwords for all your online accounts, including your UC login. By using a password manager, you can ensure that your passwords are secure and easily accessible when needed.
- Choose a reputable password manager, such as LastPass, 1Password, or Bitwarden.
- Create an account with the password manager and set up a strong master password.
- Use the password manager to generate and store unique, complex passwords for your UC login and other online accounts.
- Enable two-factor authentication for your password manager to add an extra layer of security.
By using a password manager, you can streamline the process of creating and managing strong passwords, reducing the risk of password reuse and improving the overall security of your UC login.
Step 10: Enable IP Address Restriction
IP address restriction is a security measure that allows you to limit access to your UC account based on specific IP addresses. By enabling this feature, you can ensure that only authorized devices and networks can access your account, reducing the risk of unauthorized access.
- Log in to your UC account and navigate to the "Security Settings" or "Account Access" section.
- Locate the "IP Address Restriction" or "Allowed IP Addresses" option and enable it.
- Enter the IP addresses or IP address ranges that you trust and want to allow access to your UC account.
- Consider blocking access from unknown or suspicious IP addresses to further enhance security.
By enabling IP address restriction, you can control who can access your UC account and prevent unauthorized access from unknown sources.
Step 11: Regularly Monitor Your Account Activity
Regularly monitoring your UC account activity is an essential step in identifying any suspicious behavior or unauthorized access attempts. By reviewing your account activity, you can quickly identify and address any potential security breaches.
- Log in to your UC account and navigate to the "Account Activity" or "Login History" section.
- Review the recent login attempts, including the date, time, and IP address.
- Look for any unusual or unexpected login attempts, especially from unfamiliar locations or devices.
- If you notice any suspicious activity, take immediate action by changing your password, enabling 2FA, or contacting the UC support team.
By actively monitoring your account activity, you can stay proactive in protecting your UC login and maintaining a secure online presence.
Step 12: Enable Session Management
Session management is a critical security feature that allows you to control and manage active sessions on your UC account. By enabling session management, you can remotely sign out of active sessions, ensuring that your account remains secure even if you forget to log out on a shared or public device.
- Log in to your UC account and navigate to the "Security Settings" or "Account Management" section.
- Locate the "Session Management" or "Active Sessions" option and enable it.
- Review the list of active sessions and identify any that are unfamiliar or unauthorized.
- Click on the "Sign Out" or "End Session" button to remotely sign out of any active sessions you do not recognize.
By enabling session management, you can maintain control over your UC account and prevent unauthorized access from active sessions.
Step 13: Avoid Public Computers and Unsecured Wi-Fi
Public computers and unsecured Wi-Fi networks can pose significant security risks to your UC login. When using public computers or connecting to public Wi-Fi, your personal information and login credentials may be vulnerable to interception or theft.
- Avoid accessing your UC account on public computers, as they may have malware or keyloggers installed.
- If you must use a public computer, ensure that you log out of your UC account and clear your browsing history and cookies before leaving.
- Refrain from connecting to unsecured Wi-Fi networks, as they may allow unauthorized access to your data.
- Consider using a VPN (Virtual Private Network) when connecting to public Wi-Fi to encrypt your internet traffic and protect your data.
By avoiding public computers and unsecured Wi-Fi, you can minimize the risk of your UC login being compromised.
Step 14: Enable Email Forwarding for Account Alerts
Email forwarding is a useful feature that allows you to receive account alerts and notifications directly to your personal email address. By enabling email forwarding, you can stay informed about any security-related updates or potential breaches.
- Log in to your UC account and navigate to the "Email Settings" or "Account Notifications" section.
- Locate the "Email Forwarding" or "Account Alerts" option and enable it.
- Enter your personal email address where you want to receive the account alerts and notifications.
- Review the types of alerts and notifications you want to receive, such as password reset attempts, account changes, or suspicious login attempts.
By enabling email forwarding, you can ensure that you are promptly notified of any security-related activities on your UC account.
Step 15: Regularly Update Your UC Account Information
Keeping your UC account information up-to-date is essential for maintaining a secure login experience. Outdated or incorrect information can lead to potential security vulnerabilities and hinder your ability to recover your account in case of emergencies.
- Log in to your UC account and navigate to the "Account Settings" or "Personal Information" section.
- Review and update your personal information, such as your name, email address, phone number, and emergency contact details.
- Ensure that your recovery information, such as backup email addresses or phone numbers, is accurate and accessible.
- Regularly update your security questions and answers to maintain their relevance and security.
By regularly updating your UC account information, you can ensure that your account remains secure and accessible when needed.
Step 16: Utilize Security Tools and Software
In addition to the security measures provided by the UC system, you can further enhance the security of your UC login by utilizing additional security tools and software.
- Install reputable antivirus and anti-malware software on your devices to protect against malware and viruses.
- Use a firewall to monitor and control incoming and outgoing network traffic, adding an extra layer of security.
- Consider using a password-protected screen lock or fingerprint authentication on your devices to prevent unauthorized access.
- Keep your operating system and software up-to-date with the latest security patches and updates to address any known vulnerabilities.
By utilizing these security tools and software, you can create a robust defense against potential security threats and protect your UC login.
Step 17: Educate Yourself and Stay Informed
Staying informed about the latest security trends, threats, and best practices is crucial to maintaining a secure UC login. By educating yourself, you can make informed decisions and take proactive measures to protect your account.
- Follow reputable cybersecurity blogs, websites, and news sources to stay updated on the latest security threats and prevention strategies.
- Attend cybersecurity workshops, webinars, or conferences to enhance your knowledge and learn from industry experts.
- Engage in online communities and forums dedicated to cybersecurity to exchange information and best practices with other users.
- Stay vigilant and cautious when browsing the internet, downloading files, or opening email attachments to avoid falling victim to malware


